Comprehensive RemoteIoT Device SSH Tutorial: Your Ultimate Guide
Are you looking to establish a secure connection to your RemoteIoT device using SSH? In today's interconnected world, remote access to IoT devices has become essential for managing and monitoring systems efficiently. This RemoteIoT device SSH tutorial will walk you through the entire process, ensuring you gain the skills needed to connect and manage your devices securely.
Whether you're a beginner or an experienced professional, this guide covers everything from basic setup to advanced configurations. IoT devices are becoming increasingly prevalent in various industries, and understanding how to use SSH for remote access is crucial for maintaining security and efficiency.
By the end of this RemoteIoT device SSH tutorial, you'll have the knowledge and tools necessary to establish secure connections, troubleshoot common issues, and optimize your IoT network. Let's dive in!
- Kat Timpfs Baby Due Date What You Need To Know
- New Movierulz 2025 Releases Your Ultimate Guide To The Latest Movie Scene
Table of Contents
- Introduction to RemoteIoT Devices
- What is SSH?
- Prerequisites for RemoteIoT Device SSH
- Step-by-Step RemoteIoT Device SSH Tutorial
- Common Issues and Troubleshooting
- Security Best Practices for SSH Connections
- Advanced Configurations for RemoteIoT Devices
- Recommended Tools and Software
- Use Cases for RemoteIoT Device SSH
- Future Trends in IoT and SSH
Introduction to RemoteIoT Devices
RemoteIoT devices are revolutionizing the way businesses and individuals interact with technology. These devices allow users to monitor and control systems from anywhere in the world, making them indispensable for modern infrastructure management.
Key Features of RemoteIoT Devices
- Real-time data monitoring
- Automated system updates
- Remote diagnostics and troubleshooting
- Integration with cloud platforms
Understanding how to securely connect to these devices is critical, and SSH plays a pivotal role in ensuring data integrity and security. This RemoteIoT device SSH tutorial will equip you with the necessary skills to manage your devices effectively.
- Alana Cho The Porn Industry And Its Impact
- Get Somali Telegram Links Top Channels And Groups You Need To Know
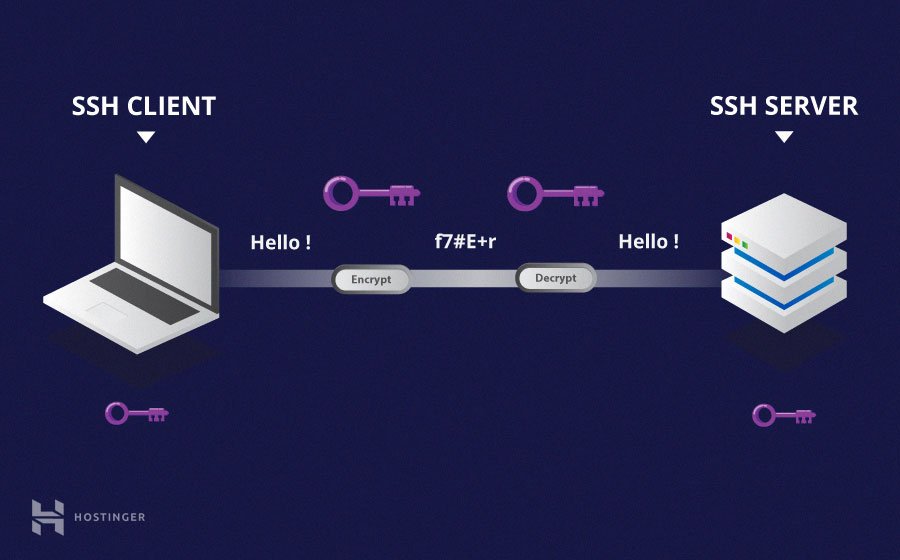
What is SSH?
SSH, or Secure Shell, is a cryptographic network protocol used for secure data communication, remote command execution, and other secure network services. It provides a secure channel over an unsecured network by encrypting all transmitted data.
Benefits of Using SSH
- Data encryption
- Authentication mechanisms
- Protection against eavesdropping
- Support for file transfer
In the context of RemoteIoT devices, SSH ensures that your connection is secure, preventing unauthorized access and potential data breaches.
Prerequisites for RemoteIoT Device SSH
Before diving into the RemoteIoT device SSH tutorial, ensure you have the following prerequisites in place:
Hardware Requirements
- A computer or laptop with SSH client installed
- A stable internet connection
- A RemoteIoT device with SSH enabled
Software Requirements
- An SSH client such as PuTTY (Windows) or OpenSSH (Linux/Mac)
- Access credentials for the RemoteIoT device
Having these prerequisites ready will streamline the process and ensure a smooth setup experience.
Step-by-Step RemoteIoT Device SSH Tutorial
This section will guide you through the process of establishing an SSH connection to your RemoteIoT device step-by-step.
Step 1: Install an SSH Client
Depending on your operating system, you may need to install an SSH client. For Windows users, PuTTY is a popular choice, while Linux and Mac users can use the built-in OpenSSH client.
Step 2: Gather Device Information
Ensure you have the IP address and login credentials for your RemoteIoT device. This information is typically provided in the device documentation or can be retrieved from the network administrator.
Step 3: Establish the Connection
Open your SSH client and enter the IP address of the RemoteIoT device. Authenticate using the provided credentials to establish a secure connection.
Step 4: Verify the Connection
Once connected, verify that you can access the device's command-line interface. This step ensures that the connection is stable and functional.
Common Issues and Troubleshooting
While setting up an SSH connection to your RemoteIoT device, you may encounter some common issues. Here are a few troubleshooting tips:
Connection Refused
Ensure that the RemoteIoT device's SSH service is running and that the firewall allows incoming connections on port 22.
Authentication Failure
Double-check your login credentials and ensure that the SSH keys are correctly configured if using key-based authentication.
Network Connectivity Issues
Verify that your internet connection is stable and that the device's IP address is correct.
Security Best Practices for SSH Connections
Security is paramount when dealing with remote access to IoT devices. Here are some best practices to enhance the security of your SSH connections:
Use Strong Passwords
Ensure that your login credentials are strong and unique. Avoid using easily guessable passwords or default credentials.
Enable Key-Based Authentication
Key-based authentication provides an additional layer of security by eliminating the need for passwords.
Limit Access
Restrict SSH access to trusted IP addresses and disable root login to minimize the risk of unauthorized access.
Advanced Configurations for RemoteIoT Devices
Once you've mastered the basics, you can explore advanced configurations to optimize your RemoteIoT device's performance and security.
Port Forwarding
Set up port forwarding on your router to allow external access to your RemoteIoT device securely.
SSH Tunneling
Use SSH tunneling to securely access services running on the RemoteIoT device, such as databases or web servers.
Automated Backups
Configure automated backups to ensure that your device's data is regularly saved and can be restored in case of failure.
Recommended Tools and Software
Several tools and software can enhance your experience when working with RemoteIoT devices over SSH:
SSH Clients
- PuTTY (Windows)
- OpenSSH (Linux/Mac)
Monitoring Tools
- Netdata
- Prometheus
These tools provide valuable insights into your device's performance and help identify potential issues before they escalate.
Use Cases for RemoteIoT Device SSH
SSH is versatile and can be applied to various use cases in the context of RemoteIoT devices:
Industrial Automation
Monitor and control industrial equipment remotely, ensuring optimal performance and reducing downtime.
Smart Home Systems
Access and manage smart home devices, such as thermostats and security systems, from anywhere in the world.
Environmental Monitoring
Collect and analyze data from sensors deployed in remote locations, providing valuable insights for environmental research.
Future Trends in IoT and SSH
As technology continues to evolve, the role of SSH in securing IoT devices will become even more critical. Emerging trends include:
Quantum-Resistant Encryption
Developing encryption methods that can withstand quantum computing attacks, ensuring long-term security for IoT devices.
AI-Driven Security
Utilizing artificial intelligence to detect and respond to security threats in real time, enhancing the protection of IoT networks.
5G Connectivity
Leveraging the increased bandwidth and reduced latency of 5G networks to improve the performance and reliability of remote IoT connections.
Kesimpulan
This RemoteIoT device SSH tutorial has provided you with a comprehensive understanding of how to establish secure connections to your IoT devices. By following the steps outlined and implementing the recommended best practices, you can ensure the security and efficiency of your network.
We invite you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT and related technologies. Together, let's build a safer and more connected future!
Article Recommendations
- Sydney Sweeney Deepfake Porn A Closer Look At The Phenomenon And Its Impact
- Mkv Cinemas Best Movies And Shows Streaming Now

Detail Author:
- Name : Pearlie Batz
- Username : catharine.crooks
- Email : adrian.dubuque@gmail.com
- Birthdate : 2006-01-07
- Address : 320 Schmitt Corner Suite 686 Lake Simeon, CT 35034-5210
- Phone : (907) 929-0971
- Company : Weissnat and Sons
- Job : Microbiologist
- Bio : Quia ipsum et vero nemo. Labore tenetur minima ducimus et. Porro aut nobis temporibus minima laudantium voluptas. In rerum excepturi commodi.
Socials
tiktok:
- url : https://tiktok.com/@bettie_hahn
- username : bettie_hahn
- bio : Et placeat omnis et fuga cum consequuntur. Id dolor ea dignissimos omnis.
- followers : 5087
- following : 2805
instagram:
- url : https://instagram.com/bettie9706
- username : bettie9706
- bio : Unde ad aperiam sed error et error. Libero quo est sapiente. Eum est nobis eos.
- followers : 1898
- following : 1885
facebook:
- url : https://facebook.com/bettie4235
- username : bettie4235
- bio : Sit vel numquam autem voluptas sequi officia.
- followers : 2056
- following : 1232
linkedin:
- url : https://linkedin.com/in/bettiehahn
- username : bettiehahn
- bio : Occaecati est enim ut illum nisi tempore.
- followers : 4927
- following : 826